- https://elasticsecurity.wordpress.com/
- https://elasticsecurity.wordpress.com/about/
- https://elasticsecurity.wordpress.com/service-offerings/
- https://outpost24.com
- https://outpost24.com/vulnerability-management
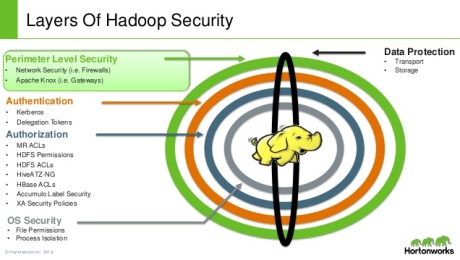
- https://elasticsecurity.wordpress.com/2016/08/10/big-data-security-how-to-secure-your-hadoop-cluster/
- https://elasticsecurity.wordpress.com/2016/05/18/how-to-creating-advanced-aws-credentials-with-iam/
- https://elasticsecurity.wordpress.com/category/aws/
- https://elasticsecurity.wordpress.com/category/iam/
- https://elasticsecurity.wordpress.com/2016/04/26/a-deeper-look-at-whatsapp-end-to-end-encryption/
- https://elasticsecurity.wordpress.com/category/discussions/
- https://elasticsecurity.wordpress.com/category/documentation/
- https://elasticsecurity.wordpress.com/category/privacy/
- https://elasticsecurity.wordpress.com/category/secure-cloud/
- https://elasticsecurity.wordpress.com/category/solutions/
- https://elasticsecurity.wordpress.com/2016/04/14/first-line-of-defense-best-security-practices-for-users/
- https://elasticsecurity.wordpress.com/2015/09/07/cloud-storage-how-to-protect-user-credentials-against-malware/
- https://elasticsecurity.wordpress.com/tag/cloud-computing/
- https://elasticsecurity.wordpress.com/2015/05/05/how-to-outsource-data-to-cloud-without-losing-confidentiality/
- https://elasticsecurity.wordpress.com/category/elastic-security/
- https://elasticsecurity.wordpress.com/category/iaas/
- https://elasticsecurity.wordpress.com/2014/07/07/having-a-look-inside-public-amazons-buckets/
- https://elasticsecurity.wordpress.com/2014/02/12/cybertech-israel-2014/
- https://elasticsecurity.wordpress.com/category/news/
- https://elasticsecurity.wordpress.com/category/presentations/
- https://elasticsecurity.wordpress.com/2014/01/24/secludit-at-fic2014/
- https://elasticsecurity.wordpress.com/2014/01/10/great-trailblazer-competition-to-start-the-year/
- https://elasticsecurity.wordpress.com/category/uncategorized/
- https://elasticsecurity.wordpress.com/2014/01/08/how-to-creating-aws-ec2-readonly-credentials-with-iam/
- https://elasticsecurity.wordpress.com/2013/12/19/backup-deduplication-encryption-cloudedup/
- https://elasticsecurity.wordpress.com/category/saas/
- https://elasticsecurity.wordpress.com/page/2/
- https://cloudyscripts.com
- http://elastic-detector.secludit.com
- http://secludit.com
- http://alestic.com/
- http://gregness.wordpress.com/
- http://aws.typepad.com/
- http://www.cloudave.com/
- http://www.shlomoswidler.com/
- http://www.cloudsecurityalliance.org/
- http://cloudsecurity.org
- http://www.rationalsurvivability.com/blog/
- http://twitter.com/SecludIT
- http://twitter.com/KaiGrunwitz
- http://twitter.com/TechRepublic
- http://twitter.com/search?q=%23CyberSecurity
- http://twitter.com/search?q=%23patchin
- http://twitter.com/SecludIT/statuses/1166403892839686146
- https://www.vice.com/en_us/article/7x5vnz/notpetya-ushered-in-a-new-era-of-malware?utm_campaign=sharebutton
- http://twitter.com/vice
- http://twitter.com/SecludIT/statuses/1166338994055057408
- https://thenewstack.io/measuring-ci-cd-adoption-rates-is-a-problem/
- http://twitter.com/SecludIT/statuses/1166236558980243457
- https://red.ht/2KyL6zv
- http://twitter.com/4enterprisers
- http://twitter.com/kevinrcasey
- http://twitter.com/SecludIT/statuses/1166236508296286209
- https://www.infoworld.com/article/3432155/how-to-stop-people-from-causing-bad-cloud-architectures.html
- http://twitter.com/infoworld
- http://twitter.com/SecludIT/statuses/1166236336619163648
- https://wordpress.com/?ref=footer_blog
Wednesday, August 28, 2019
Elastic Security | Elastic Security for Cloud Infrastructures (IaaS)
Subscribe to:
Post Comments (Atom)
No comments:
Post a Comment